CS401: Operating Systems Exam Quiz Answers
Question 1: The 64-bit logical address range is equal to which of the following? Select one:
- Less than half of the address range of a 32-bit OS
- Over 10 times that of a 32-bit OS
- 1024mb
- 4 billion 32-bit address ranges
Question 2: Which of the following introduced the capability for many users to simultaneously compete for resources? Select one:
- Batch processing
- Punched cards
- Multiprogramming
- Simplistic multiprocessors
Question 3: Fill in the blank. Computer system components may be divided into the following categories: CPU, memory, I/O modules, and _______________. Select one:
- Operating Systems
- The system bus
- Application programs
- Memory stack
Question 4: All of the following are operating systems in general use today EXCEPT: Select one:
- Unix
- Linux
- Microsoft Windows
- IOCS
Question 5: What is wrong with this diagram?
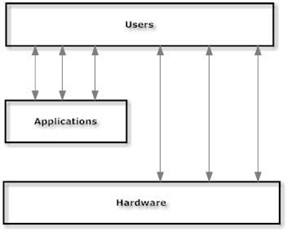
Select one:
- The operating system is missing.
- The arrows between users and hardware should be removed.
- The lines should not have double arrowheads.
- The lines between applications and hardware should be removed.
Question 6: When a thread context switch occurs, the operating system must save the state of the currently executing thread, copy all registers associated with that thread to a thread control block, and then do which of the following? Select one:
- Terminate the process.
- Restore the state of the thread to run next.
- Wait for further instructions.
- Flush all registers to disk.
Question 7: Fill in the blank. The contents of data registers, a program counter, stack pointer, open file pointers, and memory allocation are all considered to be part of the ________________. Select one:
- Hardware architecture
- Memory structure
- System bus
- Execution context
Question 8: Fill in the blank. While a process can be defined as a unit of resource ownership and pertains to the execution of a single program, a thread is a(n) ___________________. Select one:
- Set of processes
- Unit of execution which belongs to a process
- Non-traceable unit of execution
- Unit of execution which can belong to multiple processes
Question 9: Which of the following statements accurately compares threads to processes? Select one:
- Processes are independent, while threads are part of the same process and cooperate closely.
- Threads can only access a small area of memory, while processes can access a larger area of memory.
- Processes can communicate with each other, while threads cannot communicate or share information with other threads.
- A process can have at most one thread, which inherits all attributes from the process.
Question 10: What is concurrency? Select one:
- The ability of a system to handle requests sequentially
- The ability of an operating system to handle multiple tasks simultaneously
- The capability of an operating system to update itself
- The process by which user rights are managed
Question 11: In the producer/consumer problem, some threads are producers and some are consumers. While producers create items of some kind and add them to a data structurer, consumers do which of the following? Select one:
- Remove the items and store them
- Remove the items and process them
- Add more items to the data structure
- Remove items
Question 12: What are requirements pertaining to the order of events in an operating system called? Select one:
- Synchronization constraints
- Design flaws
- Data sinks
- Data flows
Question 13: One reason that there is a need for a well-structured way to facilitate inter process communication is to ensure predictable behavior. What is the other reason? Select one:
- To ensure faster operation of the system
- To avoid deadlock
- To avoid a system crash
- To maintain integrity of the system
Question 14: Choose the best answer to fill in the blanks. With share memory, interprocess communication is _____________, whereas it is ______________ for message passing. Select one:
- Internal, external
- Explicit, implicit
- Implicit, explicit
- Expensive, inexpensive
Question 15: Fill in the blank. A lock with zero or more conditional variables to manage concurrent access to shared data is called a(n) _______________. Select one:
- Monitor
- Producer
- Consumer
- Philosopher
Question 16: In the readers-writers problem, any number of readers can be in the critical section simultaneously. Which of the following statements is true about writers? Select one:
- Writers can co-exist with other writers in the critical section.
- Writers cannot enter the critical section.
- Writers must have exclusive access to the critical section.
- Writers can be in the critical section with a finite number of readers.
Question 17: All of the following are goals of the scheduler EXCEPT: Select one:
- Minimize wait time.
- Maximize throughput.
- Consume the most memory.
- Acheive fairness.
Question 18: Let’s assume that we have the following processes, arrival times and burst times:
| Process | Arrival Time | CPU Burst |
| P1 | 0 | 10 |
| P2 | 3 | 8 |
| P3 | 5 | 7 |
| P4 | 5 | 12 |
This figure shows which type of CPU scheduling algorithm?

Select one:
- First Come First Served
- Priority
- Shortest Job First
- Round Robin
Question 19: Fill in the blank. The amount of time that a process can execute is called a(n) _______________. Select one:
- CPU burst
- I/O burst
- Sun burst
- Memory cycle
Question 20: All of the following are CPU scheduling algorithms EXCEPT: Select one:
- Shortest Job Last
- Round Robin
- Shortest Time Remaining
- Shortest Job First
Question 21: While a dispatcher removes a process from the ready queue, a scheduler does which of the following? Select one:
- Removes a process from the wait queue
- Adds a process to the wait queue
- Removes all processes
- Inserts a process into a queue
Question 22: The diagram shows what kind of condition?
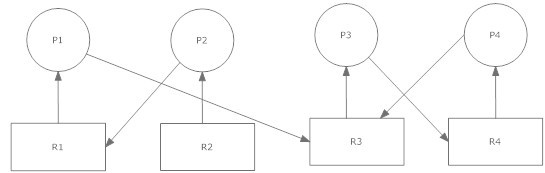
Select one:
- A race conditions
- A round robin conditions
- A deadlock conditions
- A drydock conditions
Question 23: All of the following are possible options to recover from a deadlock EXCEPT: Select one:
- Terminate a thread or process, forcing it to give up resources.
- Preempt resources without killing it off.
- Shut down the system and restart.
- Rollback actions of deadlocked threads or processes.
Question 24: In order for deadlock to occur all of the following conditions must be met EXCEPT: Select one:
- Mutual exclusion
- Hold and wait
- Non-preemption
- Rectangular wait
Question 25: In the diagram shown below, assume that the circles are processes and the rectangles are instances of a resource. Also, assume that a line from a process to a resource (i.e. the arrowhead is on the resource side) indicates that a process is requesting a resource. A line from a resource to a process (i.e. the arrowhead is on the process side) indicates that a resource has been allocated to a process. Why does this diagram show a deadlock?
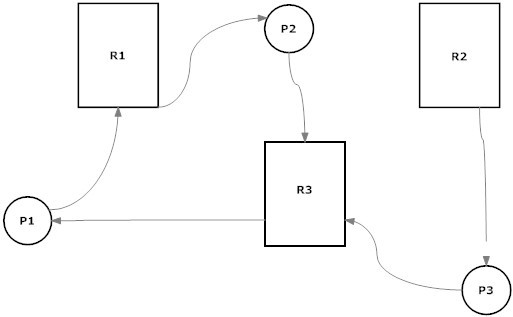
Select one:
- Resource R2 has been allocated to only one process, P3.
- Process P3 must wait for process P2 to be finished with resource R3 before it can use this resource.
- Process P1 is waiting on resource R1, which has been allocated to process P2. Process P2 is waiting for resource R3, which is currently allocated to process P1. Thus, there is a circular wait condition.
- There is no mutual exclusion present.
Question 26: Which of the following statements best describes the Banker’s Algorithm? Select one:
- The Banker’s Algorithm allocates resources dynamically to prevent deadlock.
- The Banker’s Algorithm brokers loans of resources between processes.
- The Banker’s Algorithm has never been proven to work correctly.
- The Banker’s Algorithm is best used when a large amount of memory is available.
Question 27: Fill in the blank. Translating memory references in code to actual physical memory is called _______________. Select one:
- Relocation
- Translation
- Iteration
- Transliteration
Question 28: Which of the following are requirements of memory management that the operating system must perform? Select one:
- Buffer overflow and logical mapping
- Memory allocation and subdiving memory for multiple processes
- Blocking and deallocating failed memory
- Memory protection and buffer overflow
Question 29: All of the following are part of the memory management hierarchy EXCEPT: Select one:
- Hardware memory management
- Application memory management
- Printer memory management
- Operating system memory management
Question 30: While hardware memory management is most concerned with electronic devices, such as RAM, that actually store data, operating system memory management is concerned with which of the following? Select one:
- How to request more memory from the owner of the system
- How to allocate memory to processes and reallocate it when it is no longer needed
- Fragmenting physical memory
- Only virtual memory management
Question 31: How does the operating system use virtual memory to make application programs think that they have a full 32-bit address space when physical memory is often much less? Select one:
- Ram is used to store information multiple times.
- Frequently used items are stored in RAM, while less used items are stored on disk. When needed, items from disk are brought into memory.
- Disk is directly mapped to memory addresses.
- Extremely fast disk is mapped to memory addresses.
Question 32: While the best fit algorithm scans the free memory list to find the best free hole to use for a memory request, the first fit algorithm does which of the following? Select one:
- It finds the largest free space that can accommodate the request.
- It finds the first free space that can accommodate the request.
- It finds the first free space that will exactly accommodate the request.
- It finds the first free space irregardless of whether the request will fit in the space or not.
Question 33: Assume that the disk head is currently at 50. We have the following disk cylinder requests from processes (assume that they have all arrived at the same time).
110,18,21,98,112,150,190
Using the First Come First Served algorithm, how many cylinders would the disk arm move across in total to accommodate all requests? Select one:
- 204
- 324
- 169
- 523
Question 34: Assume that the disk head is currently at 50. We have the following disk cylinder requests from processes (assume that they have all arrived at the same time).
110,18,21,98,112,150,190
Using the Shortest Seek Time algorithm, how many cylinders would the disk arm move across in total to accommodate all requests? Select one:
- 204
- 324
- 109
- 456
Question 35: All of the following are ways to access a file EXCEPT: Select one:
- Sequential access
- Parallel access
- Content-based access
- Random access
Question 36: All of the following are types of security threats EXCEPT: Select one:
- Errors and omissions
- Fraud and theft
- System failure
- Malicious hackers
Question 37: Which of the following dictates that programs, users, and systems be given just enough privileges to perform their tasks? Select one:
- Marconi Algorithm
- Fault Tolerent Principle
- Security Principle
- Principle of Least Privilege
Question 38: Fill in the blank. Self-replicating code that does not require a host program is called a(n) _________________. Select one:
- Trojan horse
- Worm
- Virus
- Modular bot
Question 39: Fill in the blank. A code segment that replicates itself by attaching copies of itself to existing executables is called a(n) _____________. Select one:
- Trojan horse
- Virus
- Worm
- Logic bomb
Question 40: Which of the following is an access control method that assigns privileges to users, programs, or roles as appropriate? Select one:
- Role-based access control
- Static access control
- Dynamic access control
- Rule-based access control
Question 41: Fill in the blank. One form of broadcast transmission, unicast, sends a message from one node to another. Another type of transmission that sends a message from one node to many is called _______________. Select one:
- Swellcast
- Multicast
- Avicast
- Plexicast
Question 42: Fill in the blank. While protocols are used to communicate between nodes, _____________ contain data encoded using a protocol. Select one:
- Packets
- Bits
- Packages
- Bytes
Question 43: Which of the following is a type of network that connects hosts within a building or campus of buildings? Select one:
- Wide-area network
- Local-area network
- Metropolitan area network
- Global network
Question 44: The TCP/IP reference model has how many layers? Select one:
- 4
- 7
- 16
- 5
Question 45: The OSI reference model has how many layers? Select one:
- 5
- 7
- 12
- 3
Question 46: Multiple protocols can be handled by a network operating system through the use of which of the following? Select one:
- Application programs
- Translators
- Buffering
- Layering
Question 47: Fill in the blank. The physical layout of a network is called its ________________. Select one:
- Physical schema
- Cabling specifications
- Topology
- Lineage
Question 48: Which of the following statements about operating systems is false? Select one:
- An operating system manages a computer system’s resources.
- An operating system is not a necessary software component of all computer systems.
- An operating system acts as an interface between hardware and application programs.
- An operating system provides a set of services to users.
Question 49: All of the following are reasons for a context switch EXCEPT: Select one:
- There is an elapsed time slice.
- A higher priority thread is ready to run.
- A running thread needs to wait.
- A running thread is stuck in a loop.
Question 50: All of the following are ways for a programmer to implement concurrency EXCEPT: Select one:
- Blocking
- Inter-process communication
- Mapping processes directly to hardware
- Select-based programming
Question 51: Consider the following pseudocode:
while True:
think ()
get_forks ()
eat ()
put_forks ()
This code best represents which of the following?
Select one:
- Moaning philosophers problem
- Producer-consumer problem
- Readers-writers problem
- Dining philosophers problem
Question 52: A race condition results when which of the following occurs? Select one:
- Two processes compete for the same resource at the same time.
- An operation depends upon the ordering of when individual processes are run.
- Two processes depend on each other to release resources that each need.
- The cpu is processing faster than memory.
Question 53: Fill in the blank. When processes communicate with one another, this is often done through the use of ______________. Select one:
- Shared memory
- Semaphores
- Morse code
- Shared files
Question 54: Which of the following best represents one of the advantages of semaphores? Select one:
- They are not expensive to implement.
- They can be written only in Java.
- They impose deliberate constraints that help programmers avoid error.
- They increase programmer productivity.
Question 55: All of the following are places where scheduling decisions may take place EXCEPT: Select one:
- When a process is deadlocked.
- When a process switches from running to waiting state.
- When a process terminates.
- When a process switches from waiting to ready.
Question 56: Fill in the blank. One of the common ways to detect deadlock is to scan the resource allocation graph and ________________. Select one:
- Recover from deadlock
- Terminate all processes
- Detect quadratic process events
- Detect circular chains of requests
Question 57: Fill in the blank. A system is in a safe state when deadlock is avoided even if the system ________________. Select one:
- Has low memory
- Is in a state of deadlock
- Lacks sufficient privileges
- Allocates resources up to the maximum for each process
Question 58: While deadlock avoidance is a strategy which only grants a resource to a process if the request will not result in deadlock, deadlock prevention does which of the following? Select one:
- Follows a strict set of rules to prevent deadlock
- Changes the rules so that processes will not make requests which will cause deadlock
- Never works correctly
- Causes only one process to execute on the processor at one time
Question 59: All of the following are page replacement algorithms EXCEPT: Select one:
- LRU
- OPT
- NRU
- Best Fit
Question 60: Fill in the blank. When a page of memory is requested and the valid bit is set to false in the page table, a __________________ occurs, and the page is retrieved from disk and swapped with another page on a frame in memory. Select one:
- Memory exchange
- Page fault
- Ram shift
- Memory optimization
Question 61: Fill in the blank. When a process spends all of its time page faulting instead of doing useful work, this is called ________________. Select one:
- Wasted time
- Memory mash
- Thrashing
- Trashing
Question 62: The diagram below shows what method of file allocation?
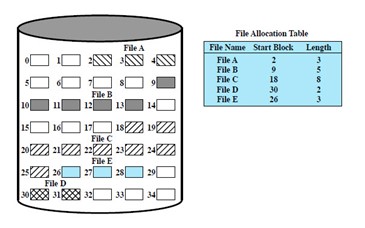
Select one:
- Indexed
- Chained
- Uniform
- Contiguous
Question 63: The resources that a process may access are specified by which of the following? Select one:
- An integrity domain
- A protection domain
- A domain fences
- A protection grids
Question 64: What is one restriction of a 32-bit kernel? Select one:
- The maximum size of an individual process
- The number of threads that can execute at once
- The size of the cache
- The link to the DMA controller
Question 65: A process can be defined as a unit of execution characterized by all of the following EXCEPT: Select one:
- A single sequential thread of execution.
- A current state.
- Exclusive control of one computer component.
- Having a set of system resources associated with it.
Question 66: Fill in the blank. Executable threads contained in a queue maintained by the scheduler are called ________________. Select one:
- Ready threads
- Processes
- Waiting threads
- Terminated threads
Question 67: Which of the following describes one objective of CPU scheduling? Select one:
- To keep the CPU free as much as possible
- To decide which threads and/or processes should be given access to resources from moment to moment
- To flush out internal caches to disk when they are full
- To schedule backup jobs for the CPI
Question 68: Let’s assume that we have the following processes, arrival times and burst times:
Process Arrival Time CPU Burst
—————————————————————–
P1 0 10
P2 3 8
P3 5 7
P4 5 12
The figure shows which type of CPU scheduling algorithm?
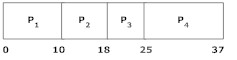
Select one:
- Shortest Job First
- First Come First Served
- Round Robin
- Priority
Question 69: A process is considered to be preemptive when it can be forced to give up the CPU. Which of the following statements about a nonpreemptive process is true? Select one:
- It can be terminated by any other process.
- It runs until it terminates or willingly gives up control.
- It never terminates.
- It always only lasts one CPU burst.
Question 70: Fill in the blank. When allocating memory, holes left over which are not big enough to satisfy any requests are called ____________. Select one:
- Fragments
- Holes
- Vortexes
- Parity bits
Question 71: While paging makes each process think that it has more memory than it really has, segmentation goes one step further by doing which of the following? Select one:
- Allowing each process to have multiple simulated memories
- Allowing each process to have more than one page fault at the same time
- Allowing each process to spawn into subprocesses
- Allowing physical memory to be split up
Question 72: Which disk scheduling algorithms perform better for systems that place a heavy load on disk? Select one:
- Shortest Seek Time First
- First Come First Served
- SCAN and C-SCAN
- Look and C-Look
Question 73: The diagram shows which type of file allocation method?
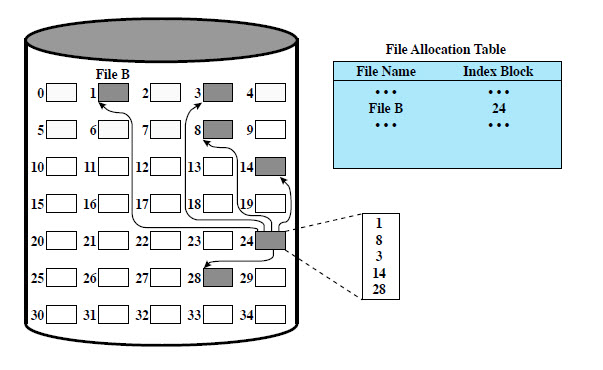
Select one:
- Contiguous
- Chained
- Indexed
- Hash key
Question 74: Two nodes on a network communicate via which of the following? Select one:
- Language
- Prototype
- Protocol
- Handshake
Question 75: All of the following are reference models EXCEPT: Select one:
- TCP/IP
- OSI
- Pyramid Reference Model
- Five Layers Model
Question 76: Fill in the blank. While physical sectors are a reality of hardware, these are abstracted in the file system to ______________. Select one:
- Logical blocks
- Named files
- Page tables
- Virtual memory
Question 77: Disk access time is composed of which of the following? Select one:
- Rotational latency and cache size
- Seek time and pause time
- Seek time and rotational latency
- Rotational latency and disk arm length
Question 78: Which computer security threat is directly related to the amount of information being stored on computers? Select one:
- Threats to personal privacy
- Malicious code
- Loss of physical infrastructure
- Errors and omissions
Question 79: Which of the following statements is true of the operating systems of the 1950’s? Select one:
- They were as good as today’s operating systems.
- Generally, they ran only one job at a time.
- They could accommodate many users at once.
- Operating systems did not exist in the 1950’s.
Question 80: Fill in the blank. The following figure shows an example of a(n) ______________. Select one:
- Fetch cycle
- Instruction cycle
- Execution cycle
- CPU cycle
Question 81: Fill in the blank. A block of code where shared resources are accessed is called a(n) ______________. Select one:
- Cache
- Heap
- Critical section
- Stack
Question 82: When thinking about an operating system, synchronization refers to which of the following? Select one:
- The way that the system clock is managed
- The way that the computer starts up
- Relationships among any number of events
- Software vs. hardware timing
Question 83: All of the following are differences between an integer and a semaphore EXCEPT: Select one:
- You cannot read the current value of a semaphore.
- A semaphore can be negative whereas an integer cannot be.
- When a thread decrements the semaphore, if the result is negative, the thread blocks itself and cannot continue until another thread increments the semaphore.
- When a thread increments the semaphore, if there are other threads waiting, one of the waiting threads gets unblocked.
Question 84: Fill in the blank. When each process or thread in a set is waiting for resources to be freed by other processes or threads in the set then ________________ occurs. Select one:
- Chaos
- Deadlock
- Controlled order
- Stack overflow
Question 85: All of the following are file system components EXCEPT: Select one:
- Page table
- Disk management
- Naming
- Reliability
Question 86: Of all of the computer security threats, which would be the hardest for an organization to control? Select one:
- Industrial espionage
- Loss of physical and infrastructure support
- Malicious code
- Hackers
Introduction to Operating Systems
Operating systems (OS) are crucial software that manage hardware and software resources on a computer. They provide a user interface and enable applications to run. Here are some key aspects and popular examples of operating systems:
Key Functions of Operating Systems
- Process Management: OS manages processes in the system, including scheduling and executing processes, handling multitasking, and ensuring smooth execution.
- Memory Management: It handles the allocation and deallocation of memory space as needed by programs. This includes virtual memory management to extend the available memory.
- File System Management: The OS manages files and directories on storage devices, including organizing, reading, writing, and permissions.
- Device Management: It controls hardware devices through drivers and provides a way for software to interact with hardware components.
- User Interface: OS provides a user interface, which can be command-line-based (CLI) or graphical (GUI), allowing users to interact with the computer.
- Security and Access Control: The OS enforces security policies to protect data and system integrity, including user authentication and authorization.
- Networking: It handles network connections, including managing network protocols and ensuring data transmission between devices.
Popular Operating Systems
Desktop Operating Systems:
- Windows: Developed by Microsoft, Windows is widely used in personal and business environments. It features a graphical interface and extensive software compatibility.
- macOS: Developed by Apple, macOS is known for its sleek design and integration with Apple’s ecosystem. It’s commonly used in creative industries.
- Linux: Linux is an open-source OS with various distributions (distros) like Ubuntu, Fedora, and Debian. It’s popular for its flexibility, security, and use in servers and embedded systems.
- Chrome OS: Developed by Google, Chrome OS is designed primarily for web-based tasks and runs on Chromebooks. It integrates tightly with Google’s services and the Chrome browser.
Mobile Operating Systems:
- Android: Developed by Google, Android is the most widely used mobile OS. It powers a wide range of devices, including smartphones and tablets.
- iOS: Developed by Apple, iOS is used exclusively on iPhones and iPads. It’s known for its security and smooth integration with Apple’s hardware.
Server Operating Systems:
- Windows Server: Microsoft’s server OS, designed for handling enterprise-level tasks such as data management, network services, and hosting applications.
- Linux Server Distributions: Many server environments use Linux due to its stability, security, and cost-effectiveness. Popular distros include CentOS, Ubuntu Server, and Red Hat Enterprise Linux.
- UNIX: A powerful, multiuser OS used in various high-performance computing environments and servers.
Embedded and Real-Time Operating Systems:
- RTOS (Real-Time Operating Systems): Designed for systems requiring timely processing, such as industrial robots, medical devices, and automotive systems. Examples include FreeRTOS and VxWorks.
- Embedded Linux: Customized versions of Linux used in embedded systems, like smart appliances and IoT devices.
Operating systems continue to evolve, addressing new challenges and incorporating advanced features to meet the growing demands of users and technology.
